Even a small bug can create a security loophole, performance issue, or system downtime. At KV IT-Solutions, we provide end-to-end bug identification and remediation services to ensure your IT infrastructure runs smoothly, securely, and without interruptions.
What We Do in Bug Fixing:
Application Bug Diagnosis: Identify coding flaws, runtime errors, and compatibility issues.
OS-Level Issue Resolution: Fix kernel errors, patch vulnerabilities, and stabilize server performance.
Software & Package Debugging: Resolve version conflicts, configuration errors, and deployment bugs.
Database Issue Resolution: Address indexing issues, query optimization, and database corruption.
Patch Management: Apply security patches promptly to eliminate known vulnerabilities.
Custom Fixes: Create tailored solutions for proprietary software and critical applications
Why It Matters:
Every bug is a potential security breach waiting to happen. Fast bug resolution ensures business continuity, improved system performance, and lower IT risks.
Network & Server Hardening Services
Lock Down Your IT Infrastructure Before Hackers Strike
Hardening is the process of eliminating security weaknesses by tightening configurations, removing unnecessary services, and enforcing strict policies. Our experts ensure servers, networks, and endpoints are fortified against modern cyber threats.
Server Hardening
Disable unused services and close open ports
Apply industry-standard security benchmarks (CIS, DISA STIG)
Secure SSH, RDP, and admin consoles
Implement firewall and intrusion prevention policies
Configure log monitoring and auditing tools
Harden web servers (Apache, Nginx, IIS) and application servers
Network Hardening
Firewall rule optimization and ACL review
IDS/IPS deployment and fine-tuning
Network segmentation and VLAN setup
VPN security review and MFA enforcement
Secure DNS, DHCP, and NAT configurations
Zero Trust Network Access (ZTNA) implementation
OS & Application Hardening
Lock down Linux and Windows servers
Enforce secure password policies and encryption
Patch management and automated updates
Harden databases (MySQL, PostgreSQL, MSSQL, Oracle)
Configure SELinux/AppArmor for Linux security
Cloud Hardening
Secure cloud infrastructure (AWS, Azure, GCP)
IAM roles and privilege reviews
Secure storage buckets and cloud-native apps
Implement cloud security posture management (CSPM)
Compliance & Best Practices
Implement ISO 27001, SOC 2, and CIS benchmarks
Prepare infrastructure for compliance audits
Security documentation and process standardization
Implement cloud security posture management (CSPM)
Vulnerability Assessment & Penetration Testing (VAPT)
Find Weaknesses Before Hackers Do
We perform in-depth Vulnerability Scans and Real-World Pentests to uncover:
Security misconfigurations and open ports
Weak authentication systems and privilege escalation risks
Web, API, and mobile app vulnerabilities (OWASP Top 10)
Cloud misconfigurations (AWS, Azure, GCP)
Internal and external attack surfaces
Why VAPT?
Identify hidden risks before attackers exploit them
Meet compliance standards like ISO 27001, GDPR, HIPAA, PCI-DSS
Get a clear, prioritized action plan with risk scores
Bug Fixing & Patch Management
Fix the Gaps That Put You at Risk
After detecting vulnerabilities, our engineers fix and patch every loophole:
OS & application-level bug fixing (Linux/Windows)
Kernel tuning, service optimization, and software patching
Database error resolution and optimization
Vulnerability patch validation and retesting
Custom fixes for proprietary or business-critical apps
Why Bug Fixing is Critical:
Scanning without fixing leaves you vulnerable. We ensure every flaw is resolved quickly so your systems stay reliable and secure.
Network & Server Hardening
Fortify Your Systems Against Future Threats
Hardening eliminates unnecessary risks by applying best practices and security benchmarks:
Disable unnecessary services & ports
Optimize firewall rules, ACLs, VPNs
IDS/IPS deployment & Zero Trust implementation
Secure SSH, RDP, admin consoles, and root accounts
Harden web servers (Apache, Nginx, IIS) and application servers
Apply CIS, NIST, and DISA STIG benchmarks for enterprise-grade security
Result:
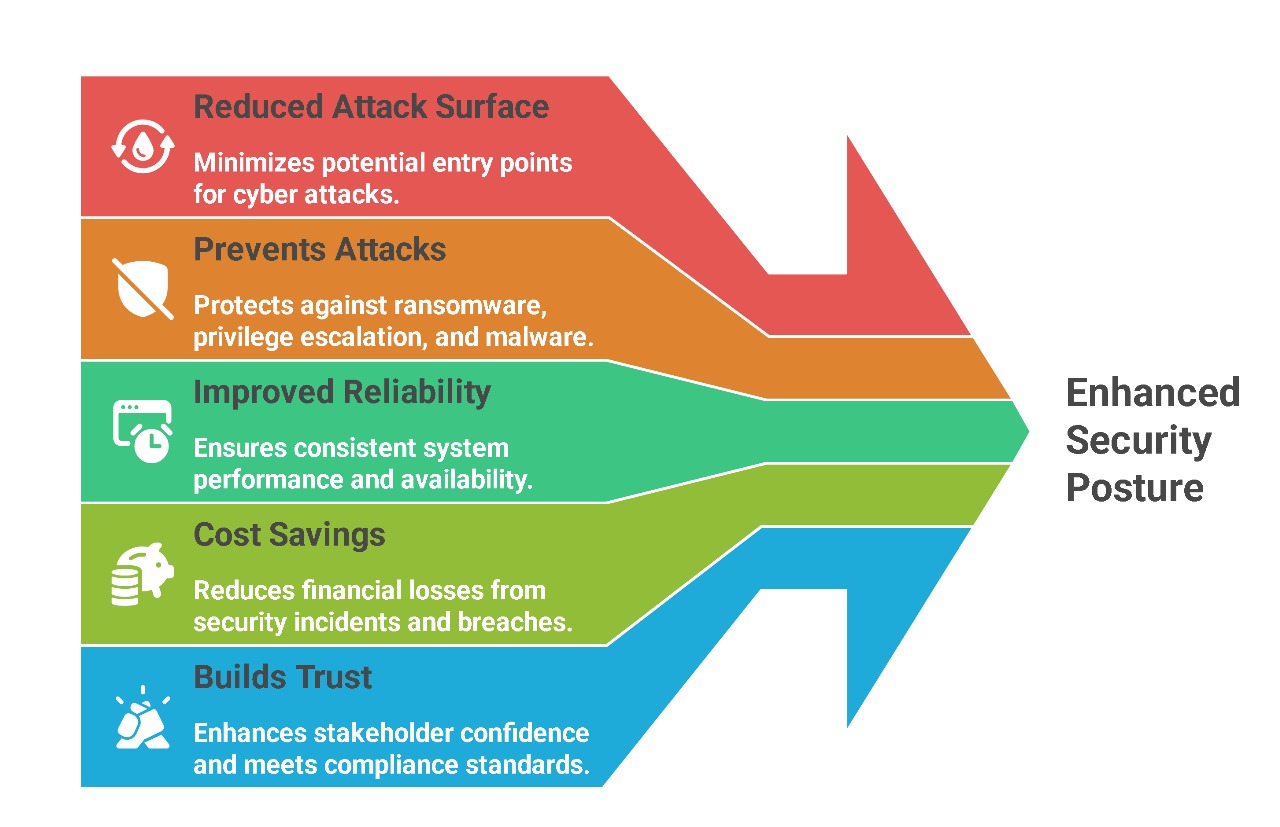
A locked-down infrastructure that is resilient against ransomware, insider threats, and advanced cyberattacks.
The KV IT-Solutions Cybersecurity Lifecycle
We don’t stop at testing; we secure and validate.
Discover: Identify vulnerabilities through automated and manual scans.
Assess: Prioritize risks and map real-world attack scenarios.
Exploit: Ethical hacking simulation to measure real impact.
Fix: Bug fixing, patching, and code-level resolution.
Harden: Apply security benchmarks, harden servers & networks.
Validate & Monitor Retesting, compliance checks, and 24/7 monitoring.


 Enquiry Now
Enquiry Now











