Linux Infrastructure Solutions for Modern Enterprises
Secure, Optimized, and Future-Ready Linux Environments
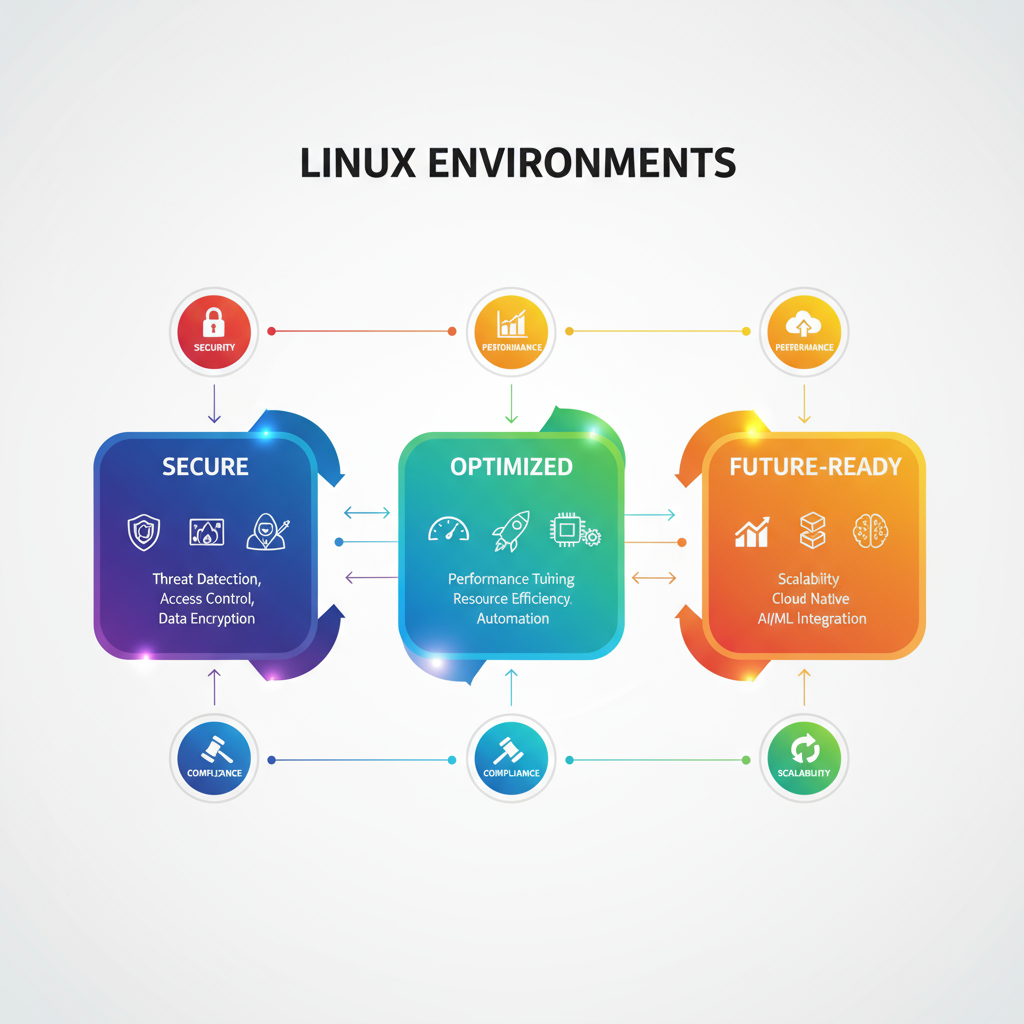
In today’s digital-first era, Linux powers the backbone of modern IT infrastructure—from mission- critical servers and databases to cloud platforms and enterprise applications. Its unmatched stability, scalability, and cost-effectiveness make it the top choice for businesses worldwide.
But as dependence on Linux grows, so do the challenges: cybersecurity threats, stringent compliance requirements, and the need for 24/7 uptime. Deploying Linux alone isn’t enough—your systems must be secured, optimized, and ready to scale for the future.
At KV IT-Solutions, we specialize in transforming Linux environments into high-performance, secure, and compliant infrastructures. Our certified Linux experts ensure your systems deliver:
With KV IT-Solutions, your Linux environment isn’t just managed—it’s fortified, compliant, and engineered to power your business forward.
Why Choose Our Linux Infrastructure & Security Solutions?
Our Core Services
Linux Server Hardening
A secure server is the backbone of any IT infrastructure. Linux server hardening focuses on eliminating unnecessary risks and ensuring that your system runs only the most secure and required components.
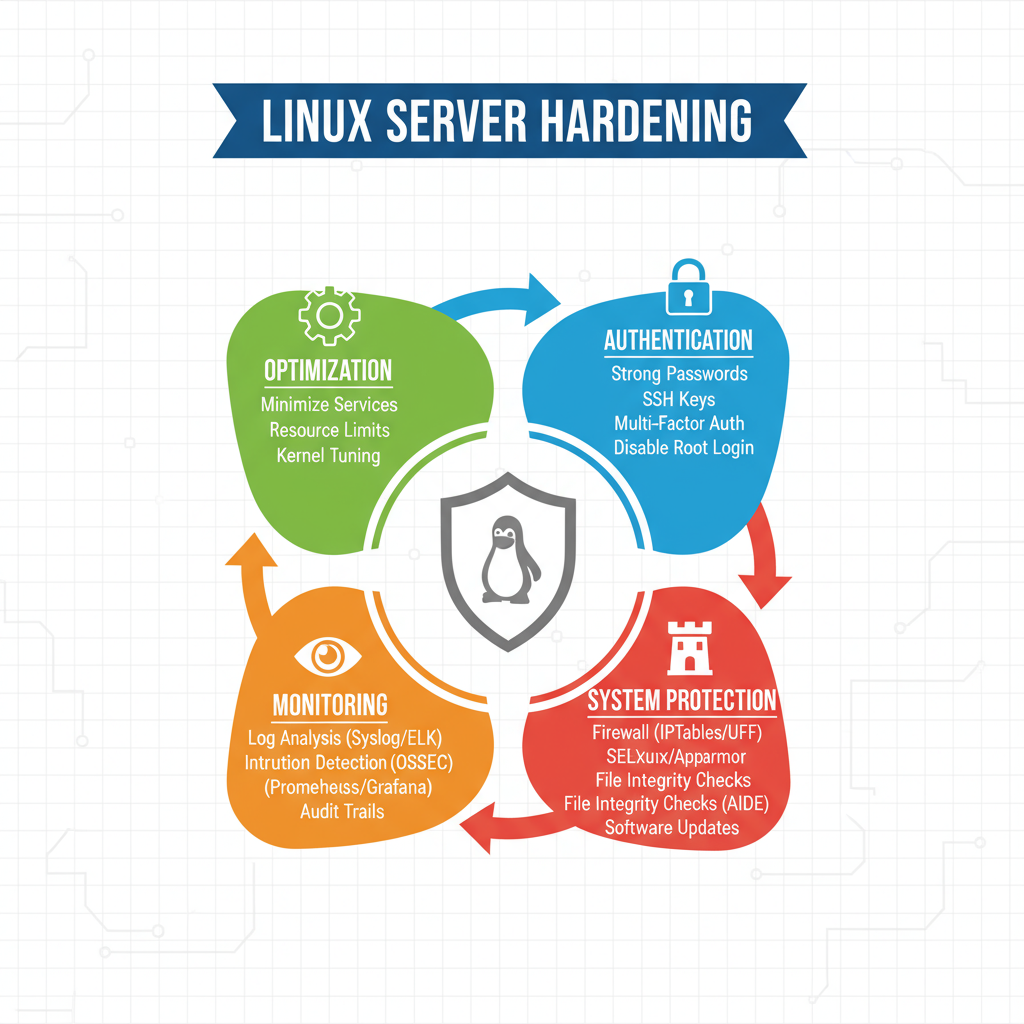
Impact: Stronger servers mean fewer vulnerabilities, reduced chances of breaches, and improved reliability of your core applications.
OS & Service Security
Every business relies on OS and critical services like SSH, web servers, DNS, and databases. A single weak configuration can open the door for attackers. Our approach ensures that every service is secured and hardened.
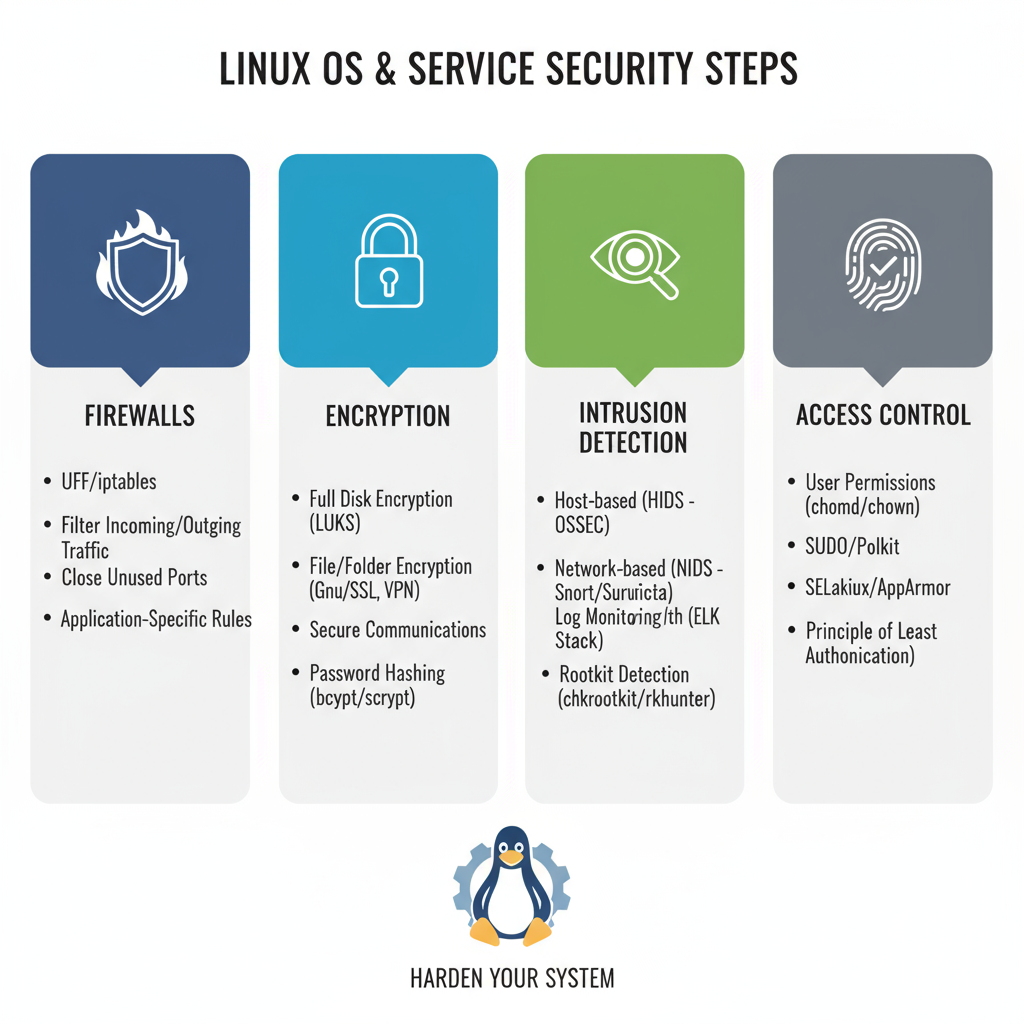
Impact: Reduces the risk of downtime, protects sensitive data, and ensures business continuity.
File, Directory & Application-Level Security
Your business data is your biggest asset. From sensitive customer information to proprietary code, every file and application needs multi-layered protection.
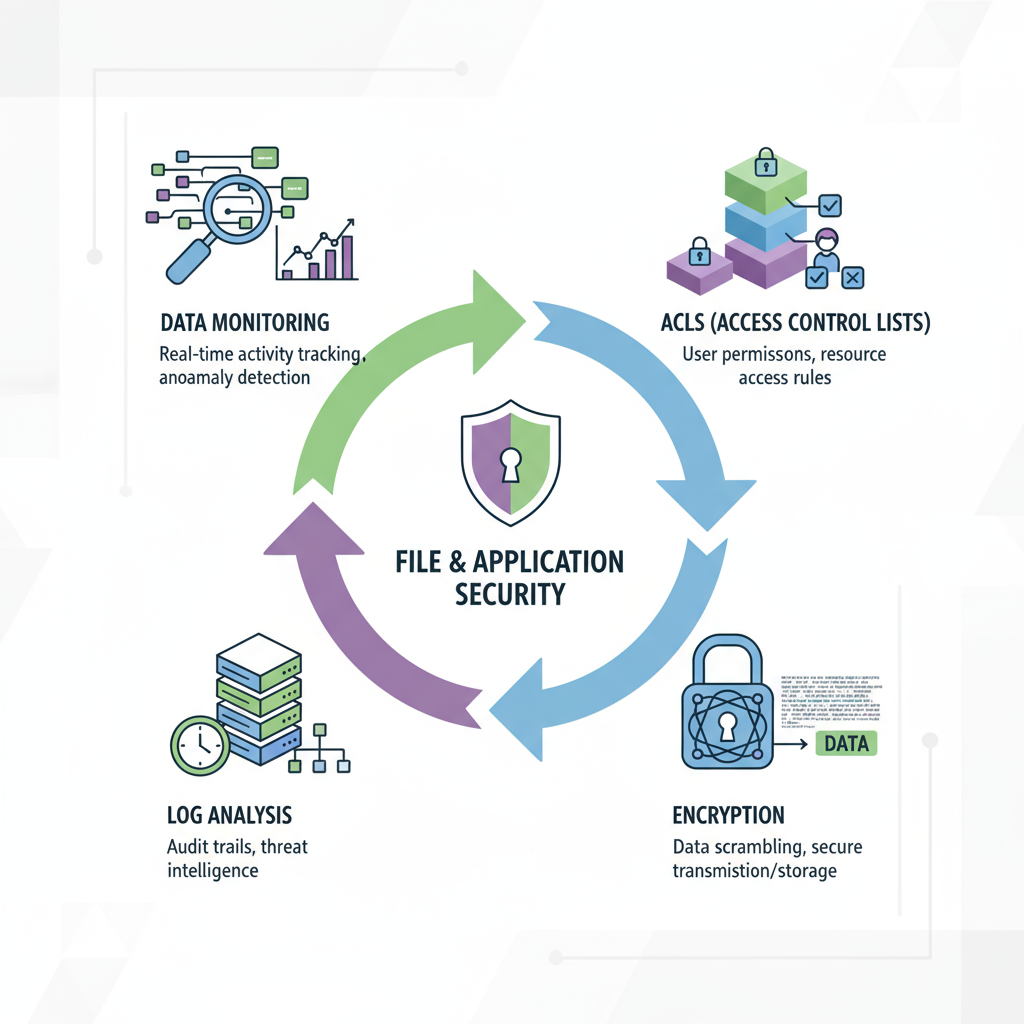
Impact: Prevents data theft, ensures secure application operations, and builds customer trust.
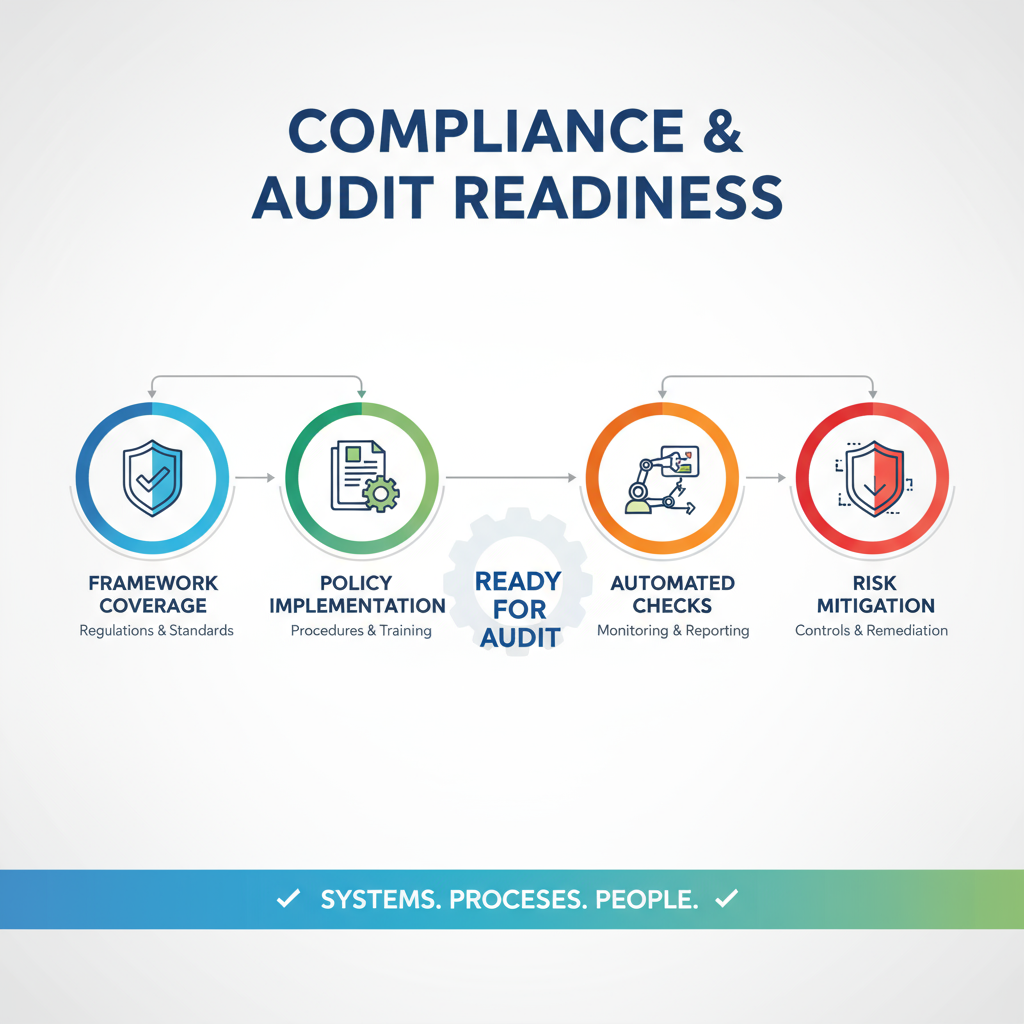
Compliance & Audit Readiness
In today’s digital world, being compliant with international security standards is not just a requirement but a necessity for business growth.
Impact:Ensures regulatory compliance, avoids penalties, builds credibility with clients, and enhances organizational reputation.
Challenges Businesses Face Without Linux Security
Our Approach to Securing Linux Infrastructure
We follow a proven step-by-step methodology to protect your business:
Assessment – Conduct detailed audits of existing Linux servers & services
Planning – Identify risks and prepare a customized hardening strategy
Implementation – Apply security patches, deploy monitoring tools, and enforce policies
Validation – Perform compliance checks and penetration testing
Ongoing Support – Provide 24/7 monitoring, patch management, and threat response
Why Partner With Us?
Core Linux Infrastructure Security Capabilities
“Let’s build a secure, compliant, and future-ready Linux infrastructure for your business.”
At KV IT-Solutions, we don’t just manage Linux infrastructure—we fortify it. Our solutions ensure your servers are hardened, your data is protected, your operations stay compliant, and your business is always up and running.
Whether you are modernizing your IT stack, preparing for audits, or defending against cyber threats, KV IT-Solutions is your trusted Linux partner.

Testimonials
 Enquiry Now
Enquiry Now











