"Secure. Optimize. Monitor. — Keep Your OS & Services Resilient with KV IT-Solutions."
Reliable | Secure | Open-Source
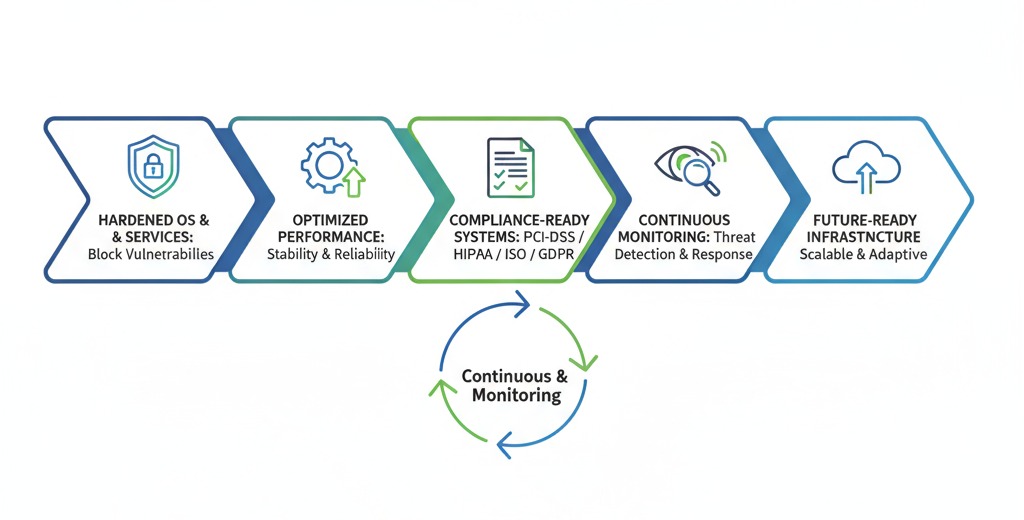
In today’s fast-evolving digital landscape, operating systems and critical services form the backbone of enterprise IT infrastructure. From Linux and Windows servers to cloud-hosted platforms, these systems support mission-critical applications, databases, and services that drive business operations. However, even minor misconfigurations, outdated patches, or unsecured services can create serious vulnerabilities, exposing your infrastructure to cyberattacks, unauthorized access, data breaches, and costly regulatory penalties.
At KV IT-Solutions, we deliver end-to-end OS and service security solutions designed to safeguard your systems, maximize performance, enforce industry compliance, and future-proof your IT environment. Our approach goes beyond basic protection—we focus on proactive threat prevention, continuous monitoring, and optimized configurations, ensuring your infrastructure is always secure, reliable, and ready for growth.
With KV IT-Solutions, your organization can achieve:
By securing your OS and services with KV IT-Solutions, your IT environment is not only protected against modern threats but also optimized for performance, compliance, and long-term business success.
Why OS & Service Security is Critical
Neglecting OS and service security can put your business at serious risk:
- Exposed vulnerabilities: Attackers can exploit unprotected systems.
- Misconfigured services: Can cause downtime or degraded performance.
- Non-compliance penalties: Violations of industry regulations.
- Inefficient patching: Leads to unpatched security gaps.
Proper OS and service security ensures resilient, compliant, and high-performing IT infrastructure.
Core OS & Service Security Services
At KV IT-Solutions, we provide comprehensive OS & Service Security services designed to secure your operating systems, critical services, and applications while optimizing performance and ensuring compliance. Each service targets a critical layer of your IT infrastructure to reduce risk and maintain seamless operations.

Operating System Hardening
Securing your OS forms the foundation of overall infrastructure security, preventing unauthorized access and system compromise.
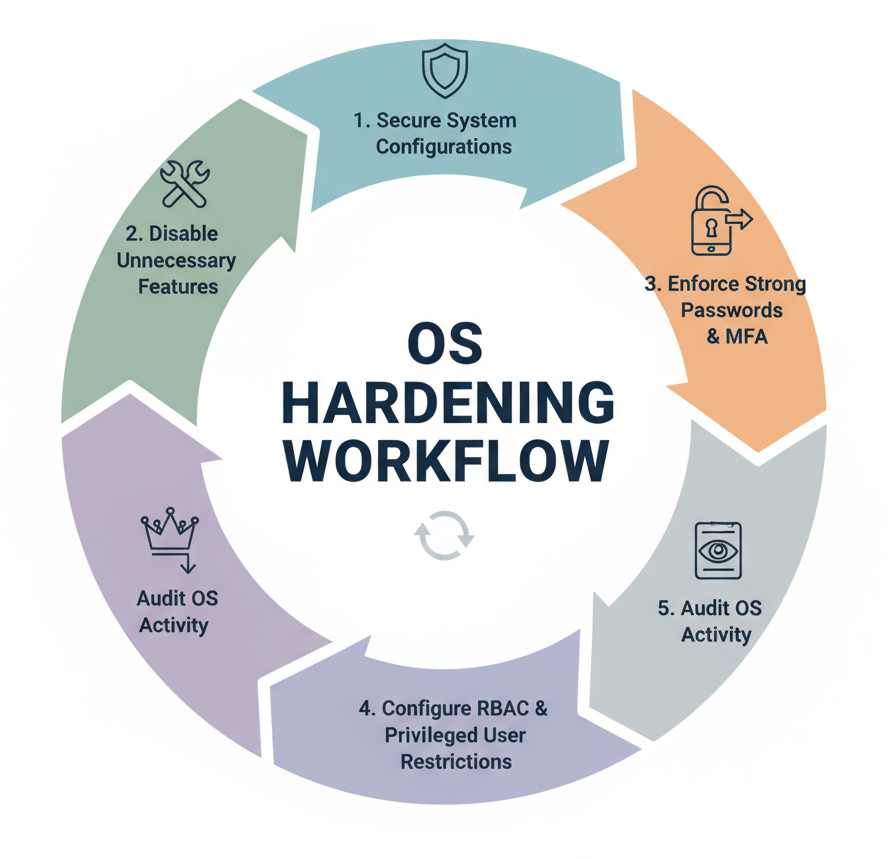
“Impact: Ensures a solid, secure foundation for your infrastructure, reduces unauthorized access, and protects critical system resources.”
Service & Application Hardening
Protecting critical services and applications reduces attack surfaces and prevents exploitation of misconfigurations.
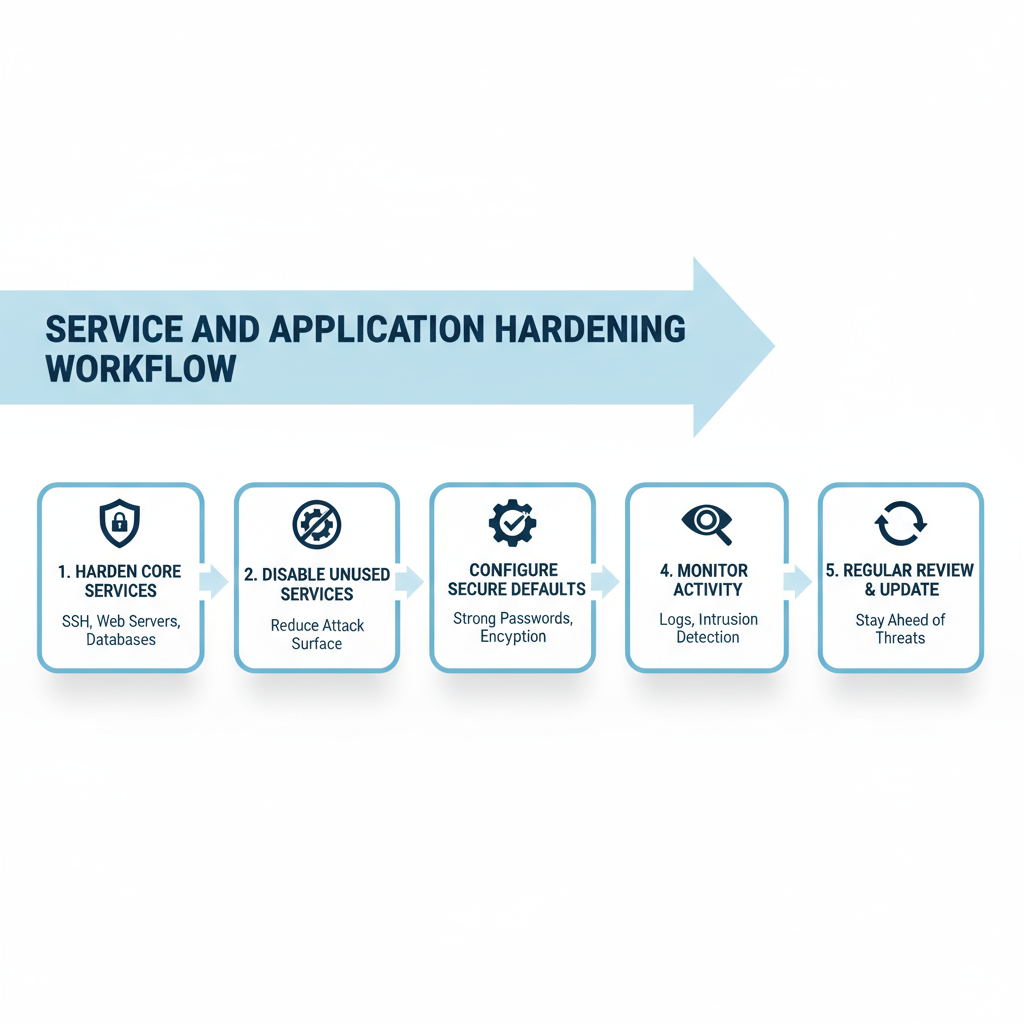
“Impact: Minimizes vulnerabilities, secures essential services, and prevents exploitation of misconfigured applications.”
Patch Management & Update Automation
Keeping OS and services up-to-date ensures protection against known vulnerabilities and regulatory compliance.
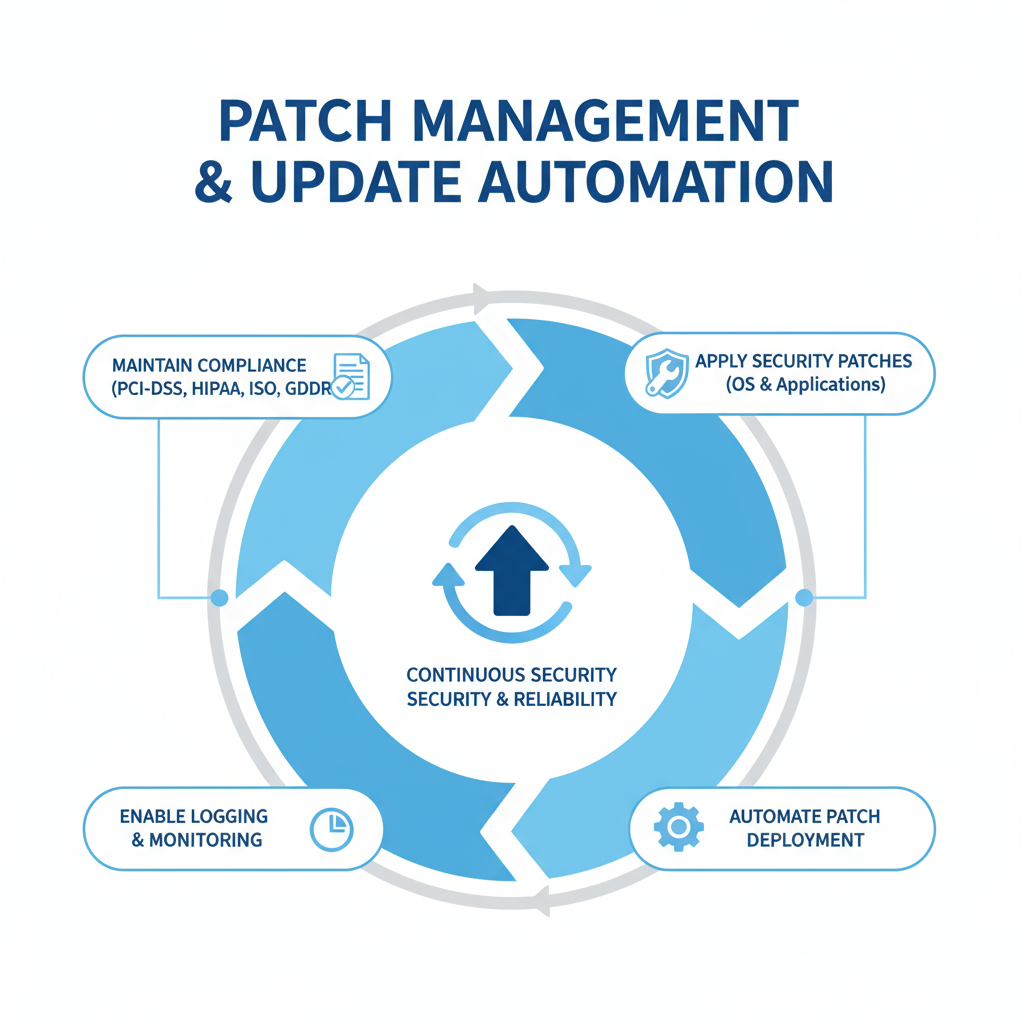
Impact: Protects systems from emerging threats, ensures compliance, and keeps infrastructure stable and reliable.
Network & Service Access Security
Secure network access to OS and services prevents unauthorized connections and lateral movement within your infrastructure.
.png)
Impact: Blocks unauthorized access, safeguards sensitive data, and strengthens the network perimeter against attacks.
Advanced Security Techniques
Enhance protection with layered security and proactive threat prevention strategies.
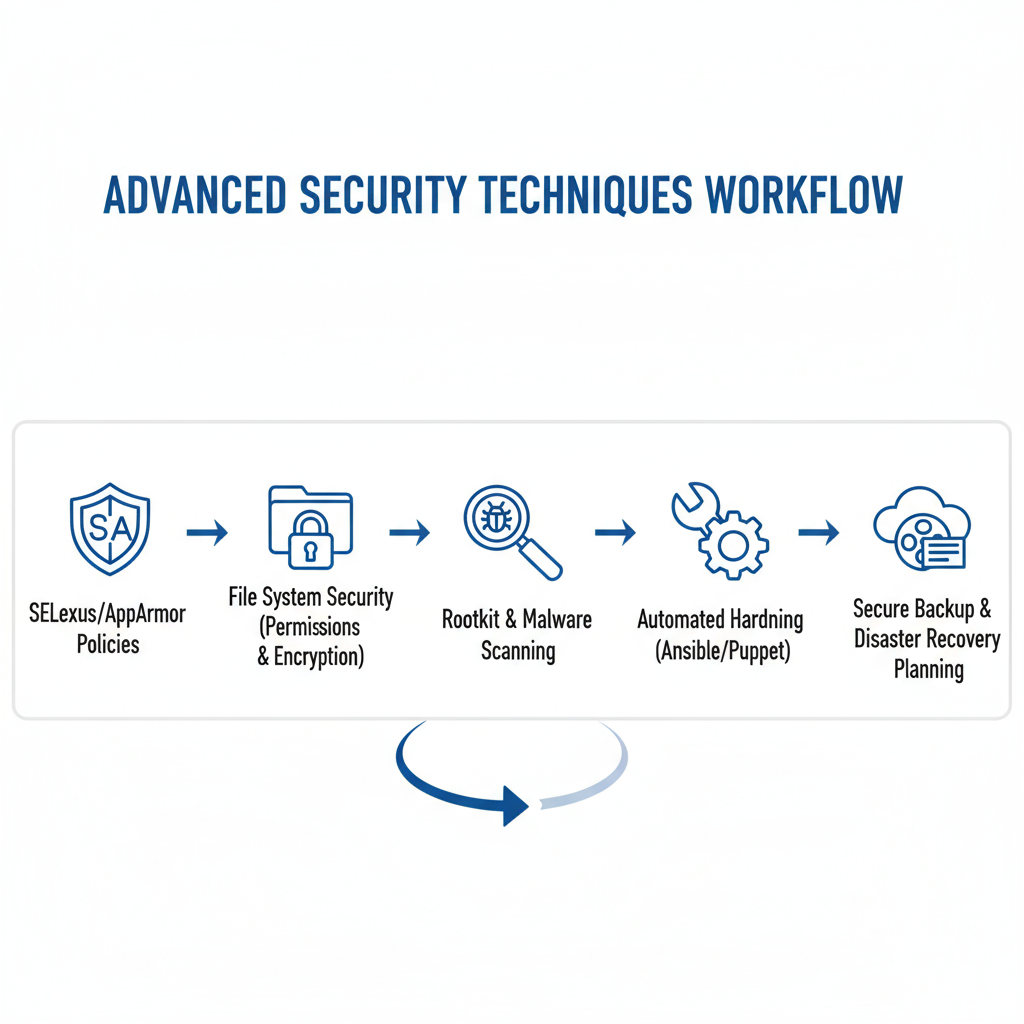
Impact: Provides multi-layered defense against sophisticated threats, ensuring resilient, continuously protected infrastructure.
Continuous Monitoring & Compliance
Maintain a secure and compliant environment through ongoing monitoring and assessment.
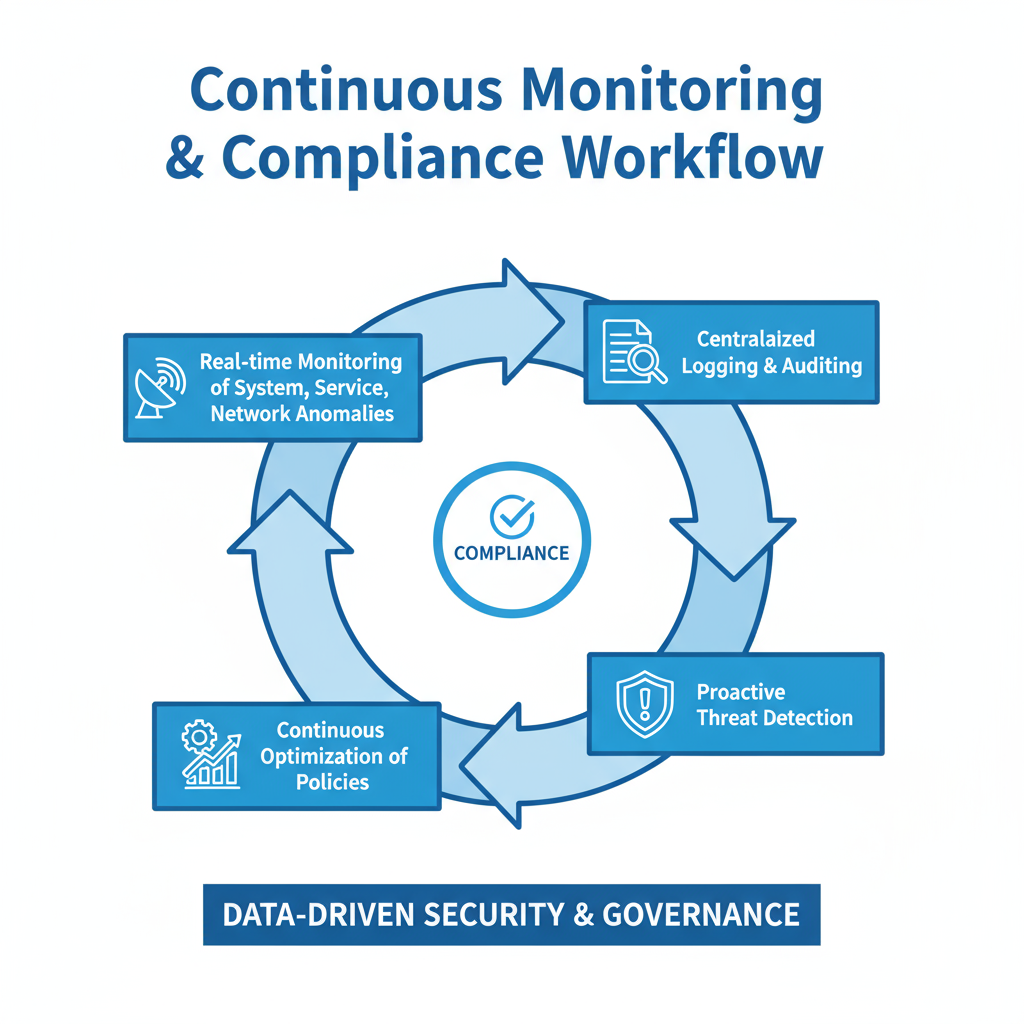
Impact: Enables proactive issue detection, maintains uptime, ensures compliance, and continuously strengthens security posture.
Advanced Security Techniques
Enhance infrastructure protection with multi-layered security strategies and proactive threat prevention:
- Restrict services to only required resources
- Prevent privilege escalation and unauthorized modifications
- Tools: rkhunter, Lynis, chkrootkit
- Continuous scanning for malware and rootkits
- Use Ansible, Puppet, or custom scripts for consistent security
- Automate patching, updates, and configuration checks
- Encrypted backups with redundancy
- Rapid recovery in case of failure or breach
- Real-time alerts for unusual activity
- Rapid threat containment and remediation
- Proactive system performance monitoring
Benefits of OS & Service Security
- Enhanced Protection – Guard against unauthorized access, malware, and vulnerabilities
- Optimized Systems – Improved efficiency and performance of OS and services
- Compliance Ready – Maintain PCI-DSS, HIPAA, ISO, GDPR compliance effortlessly
- Continuous Uptime – Minimize downtime and service interruptions
- Scalable & Future-Ready – Infrastructure ready for growth, cloud adoption, and digital transformation
Challenges Without Proper OS & Service Security
- Vulnerabilities and misconfigurations exposing systems to attacks
- Downtime and reduced operational efficiency
- Regulatory penalties due to non-compliance
- Lack of automated patching and monitoring
KV IT-Solutions Approach
Assessment – Evaluate OS, services, applications, and security posture
Planning – Design a customized OS and service security strategy
Implementation – Harden systems, secure services, deploy IDS/IPS, and enforce compliance
Validation – Perform audits, penetration testing, and performance checks
Ongoing Support – Continuous monitoring, updates, and incident management
Frequently Asked Questions (FAQs) – OS & Service Security
Core Linux Infrastructure Security Capabilities
“Defend, Optimize, and Monitor — Secure Your Operating Systems & Services Today!”
“With KV IT-Solutions, your operating systems and critical services are secure, optimized, and continuously monitored. Protect your infrastructure, ensure compliance, and maintain peak performance—so your business can focus on growth without IT risks.”

Testimonials
 Enquiry Now
Enquiry Now











