Firewall & Network Security (iptables, nftables, IDS/IPS)
.png)
Efficient firewall and network security is the cornerstone of Linux infrastructure protection. Misconfigured firewalls or lack of intrusion detection exposes critical systems to cyberattacks, unauthorized access, and data breaches. At KV IT-Solutions, we implement iptables, nftables, and IDS/IPS to provide layered, proactive, and scalable network security for servers, virtual environments, and enterprise networks.
With our solutions, your organization can achieve:
🔒 Understanding Our Network Security Tools
iptables
iptables is a Linux-based firewall tool that acts as a gatekeeper for your server’s network traffic. It filters incoming and outgoing connections based on rules you define, helping prevent unauthorized access. By controlling traffic at the kernel level, it ensures your system communicates securely with trusted sources while blocking malicious attempts.
How it works:
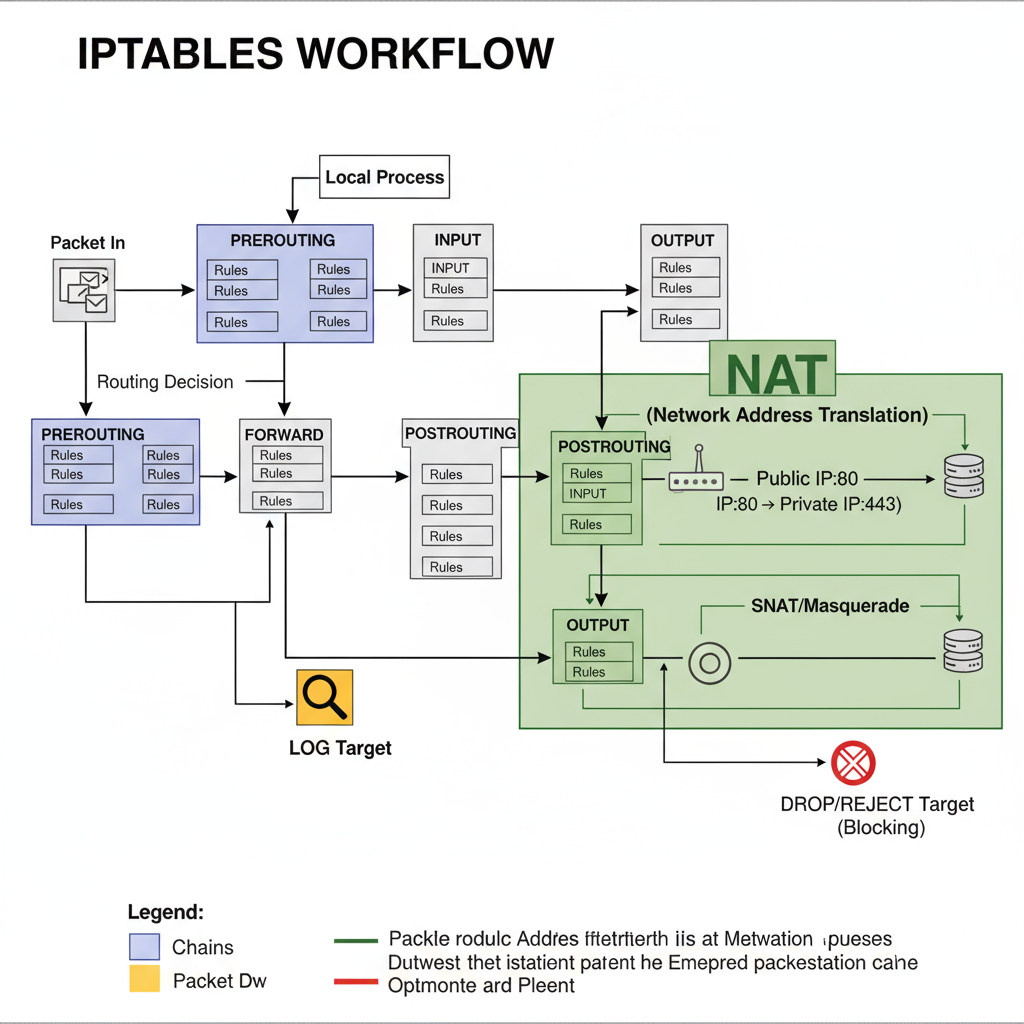
Why it matters: Keeps your Linux servers secure by preventing unauthorized access and ensuring only safe traffic flows through your network.
nftables
nftables is the next-generation Linux firewall framework designed to replace iptables. It provides a faster, simpler, and more flexible way to secure your network by organizing traffic filtering rules in a structured manner. nftables enables easier management of complex network configurations while improving performance and logging capabilities.
How it works:
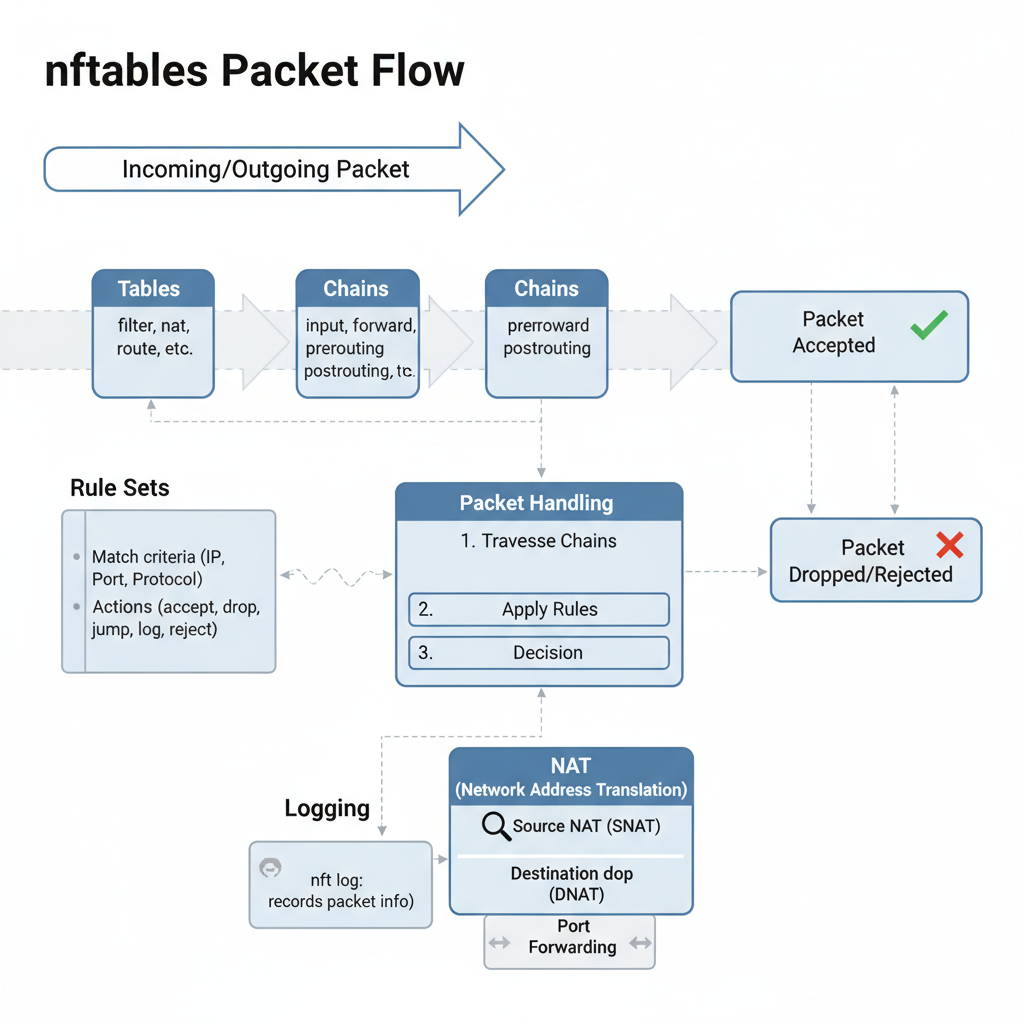
Why it matters: Provides a scalable, high-performance firewall solution that protects modern IT environments with fewer complexities.
IDS/IPS (Intrusion Detection & Prevention Systems)
IDS/IPS systems monitor network traffic to detect unusual or malicious activity in real-time. IDS identifies suspicious patterns, while IPS can actively block threats before they impact your systems. Together, they provide a proactive defense layer, ensuring that potential attacks are caught early and your network remains secure.
How it works:
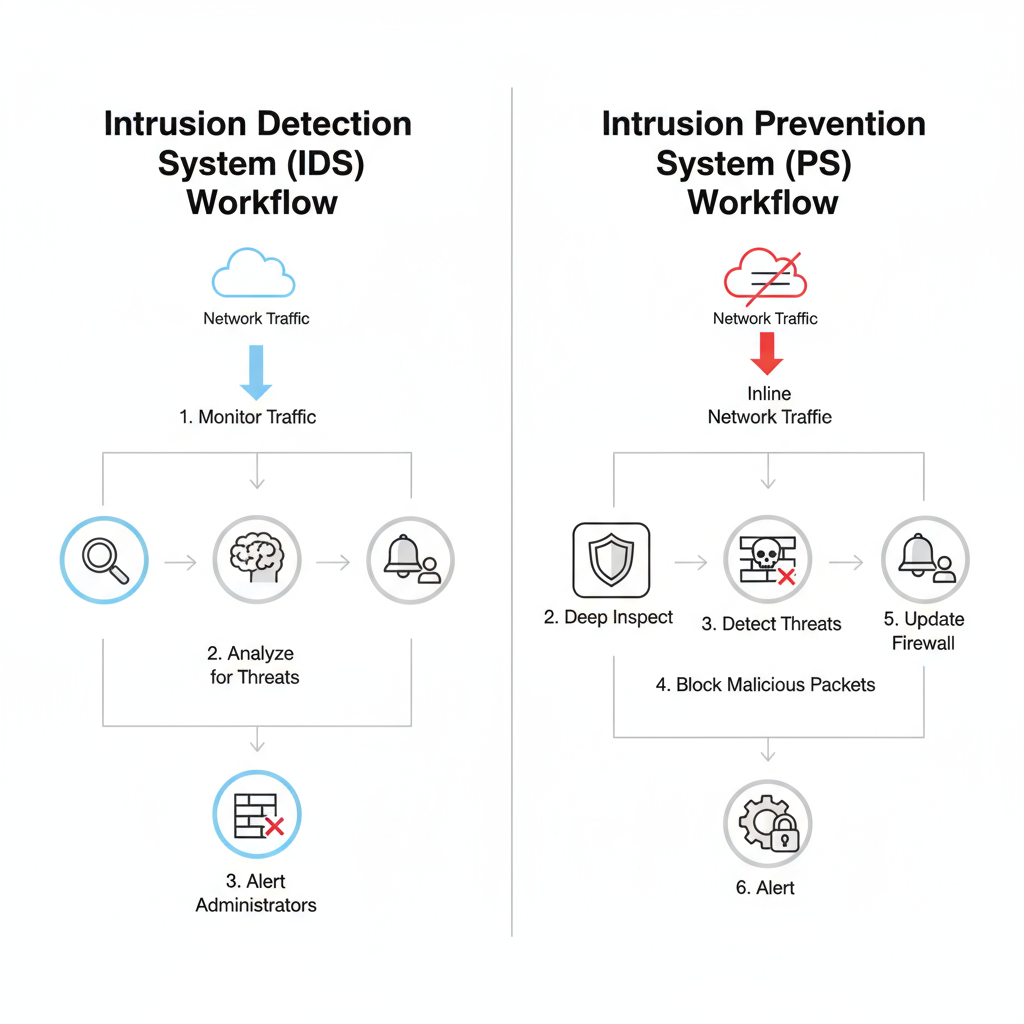
Why it matters: Adds a proactive layer of defense, stopping malware, ransomware, and intrusions before they can affect your business.
Core Firewall & Network Security Services
At KV IT-Solutions, we deliver multi-layered network security solutions to protect, monitor, and optimize your IT infrastructure. Combining advanced firewall configurations, real-time intrusion detection, and continuous monitoring, we ensure your servers, endpoints, and networks remain secure, compliant, and high-performing.
1. iptables & nftables Firewall Configuration
Definition: Configure and manage Linux-based firewalls to control traffic, enforce security policies, and prevent unauthorized access.
- Define inbound/outbound traffic rules
- Implement NAT and port forwarding
- Manage stateful connections and logging
Impact: Blocks threats, controls traffic, and ensures network integrity
2. Intrusion Detection & Prevention Systems (IDS/IPS)
Definition: Continuously monitor network traffic, detect unusual patterns, and block threats in real-time.
- Monitor network packets for anomalies
- Configure automated alerts and preventive actions
- Integrate with firewall policies for unified defense
Impact: Prevents attacks, protects sensitive data, and reduces downtime
3. Network Traffic Monitoring & Analytics
Definition: Observe and analyze network traffic to identify bottlenecks, unusual activity, and performance issues.
- Use tools like Suricata, Snort, or custom scripts
- Analyze traffic patterns, logs, and alerts
- Generate actionable reports for administrators
Impact: Enhances visibility, identifies threats, and improves network efficiency
4. Advanced Security Hardening & Policy Enforcement
Definition: Strengthen servers, network devices, and endpoints by applying consistent security policies and hardening measures.
- Enforce segmentation, ACLs, and secure routing
- Harden firewalls and services against vulnerabilities
- Apply continuous patching and updates
Impact: Reduces attack surface, enforces compliance, and strengthens resilience
5. Automation & Incident Response
Definition: Implement automated workflows to quickly respond to security incidents and streamline network operations.
- Integrate automated rule updates and alerts
- Establish incident response workflows
- Conduct regular audits and vulnerability assessments
Impact: Speeds response, reduces human error, and maintains continuous protection
Benefits of Firewall & Network Security
- Prevent unauthorized access and cyberattacks
- Ensure high availability and minimal downtime
- Maintain compliance with PCI-DSS, HIPAA, ISO, GDPR
- Optimize resource usage across servers and network devices
- Gain full visibility into network activity and security posture
Challenges Without Proper Firewall & IDS/IPS
- Vulnerable servers exposed to attacks
- Undetected intrusions causing data breaches
- Downtime from misconfigured traffic rules
- Non-compliance with regulatory standards
- Inefficient resource allocation and network congestion
KV IT-Solutions Approach
Assessment – Analyze servers, networks, and traffic patterns
Planning – Design tailored firewall and IDS/IPS strategy
Implementation – Deploy iptables/nftables and IDS/IPS solutions
Testing & Validation – Audit rules, monitor alerts, optimize performance
Ongoing Support & Updates – Continuous monitoring, patching, and improvement
FAQs – Firewall & Network Security
"Secure Your Network, Detect Threats, Stay Compliant — Empower Your IT Infrastructure Today!"
Safeguard your Linux servers and network infrastructure with KV IT-Solutions’ firewall and IDS/IPS expertise. Prevent attacks, monitor traffic proactively, and maintain compliance effortlessly.

 Enquiry Now
Enquiry Now











