File, Directory & Application-Level Security
Protect Your Data, Directories, and Applications from Modern Threats
“Over 60% of breaches start with unprotected files or misconfigured applications—don’t let your business be next.”
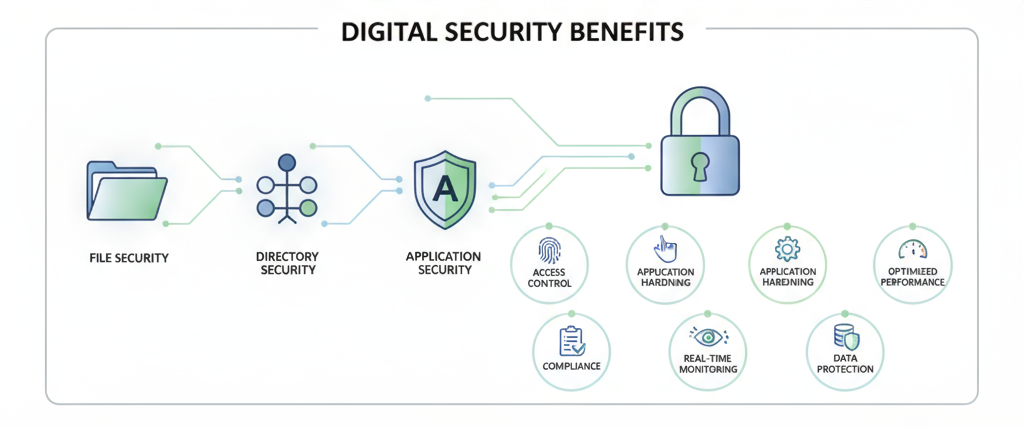
Files, directories, and applications form the backbone of enterprise IT operations, and any vulnerability can lead to data breaches, operational downtime, and compliance violations. From improper permissions to unsecured applications and sensitive data exposure, threats are constant and evolving.
At KV IT-Solutions, we provide comprehensive, end-to-end security solutions at the file, directory, and application level, designed to fortify your critical assets, optimize performance, and ensure compliance. With proactive monitoring and advanced hardening techniques, your IT environment becomes resilient, secure, and audit-ready.
Key Benefits:
- 🔐 Ironclad Access Control – Enforce least-privilege policies to prevent unauthorized access
- 🛡️ Advanced Application Hardening – Protect apps from exploits, misconfigurations, and emerging threats
- ⚡ Optimized Performance – Streamline file and directory management without slowing down operations
- 📋 Compliance-Ready Systems – Fully aligned with PCI-DSS, HIPAA, ISO, and GDPR
- 🔄 Real-Time Monitoring & Threat Response – Detect anomalies instantly and respond proactively
Core File, Directory & Application Security Services
At KV IT-Solutions, we deliver comprehensive file, directory, and application-level security services to safeguard critical business data, optimize performance, and ensure compliance with industry standards.
File & Directory Permissions Management
Ensuring proper permissions and access control for files and directories is critical to prevent unauthorized access, accidental modifications, and data breaches.
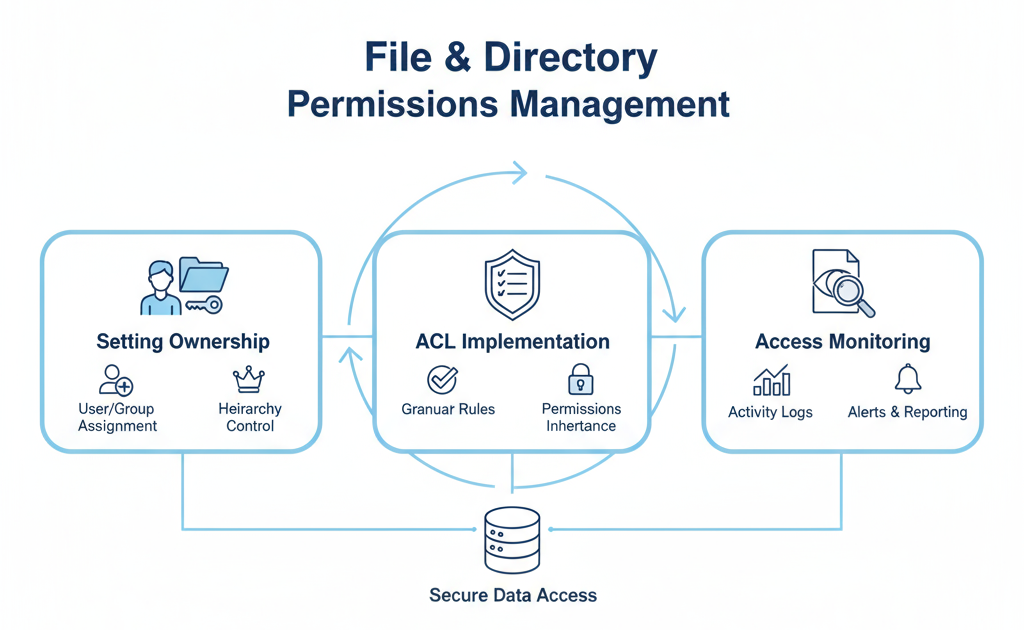
Impact: Prevents unauthorized access, data leaks, and accidental modifications.
Application-Level Security Hardening
Hardening applications strengthens their defenses against attacks, misconfigurations, and vulnerabilities that could compromise sensitive data.
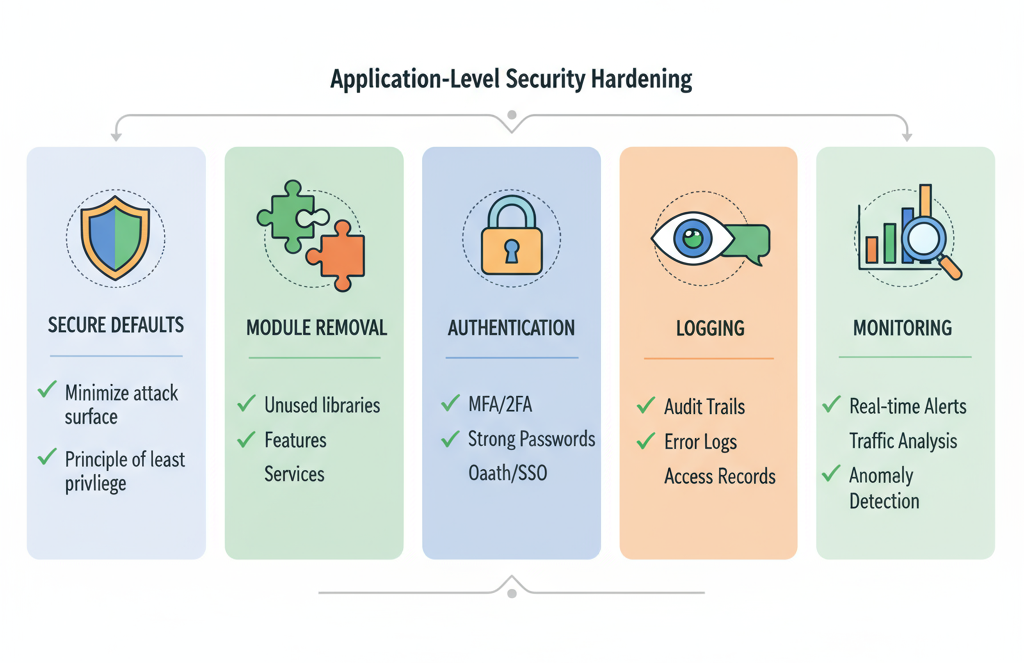
Impact: Reduces application vulnerabilities and protects sensitive data.
Data Encryption & Integrity
Encrypting and validating data ensures confidentiality, prevents tampering, and maintains the integrity of files, directories, and application data.
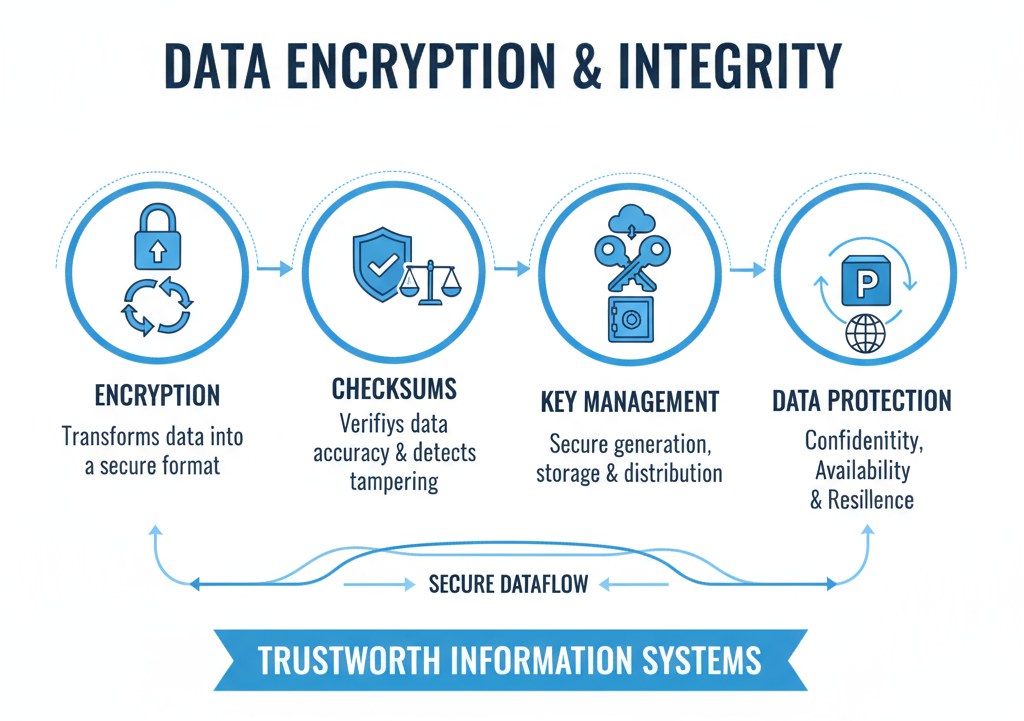
Impact: Protects sensitive data from theft, tampering, and unauthorized access.
Auditing & Compliance Monitoring
Regular auditing and monitoring maintain accountability, detect anomalies early, and help meet industry and regulatory compliance standards.
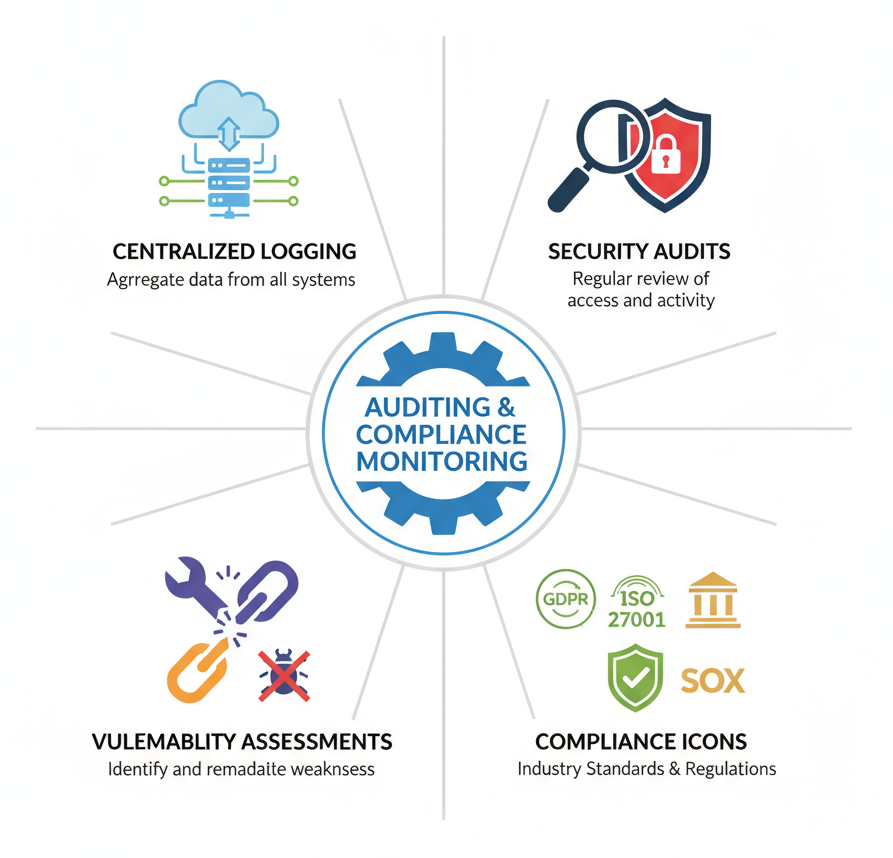
Impact: Supports accountability, compliance, and proactive risk management.
Backup & Recovery Security
Secure backups and tested recovery processes ensure business continuity and minimize data loss in the event of attacks, failures, or disasters.
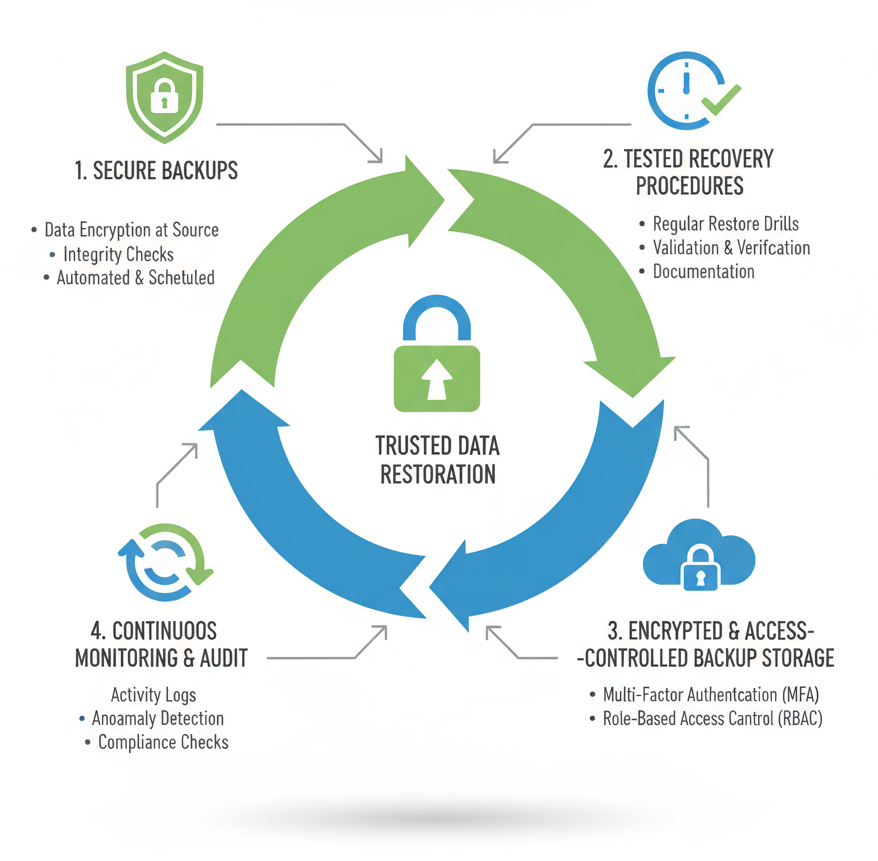
Impact: Guarantees recoverability and resilience in case of data loss or cyber incidents.
Advanced Techniques
Provides multi-layered defense against advanced threats and ensures continuous protection.
2.png)
Impact: Provides multi-layered defense against advanced threats and ensures continuous protection.
Challenges Without Proper Security
Our Approach
FAQs – File, Directory & Application-Level Security
Core Linux Infrastructure Security Capabilities
“ Secure Your Data & Applications — Protect, Monitor, and Optimize with KV IT-Solutions Today!”
Ensure your files, directories, and applications are protected, compliant, and resilient with KV IT- Solutions. Reduce risk, safeguard sensitive data, and maintain business continuity.

Testimonials
 Enquiry Now
Enquiry Now











