Linux Server Hardening – Secure, Compliant, and Optimized
Fortify Your Linux Infrastructure, Protect Your Data, and Ensure Compliance
In today’s cyber-threat landscape, Linux servers power the backbone of critical business operations— from databases and web servers to cloud platforms and enterprise applications. But as your reliance on Linux grows, so do the risks: unauthorized access, malware, misconfigurations, and compliance violations can threaten your business and compromise sensitive data.
At KV IT-Solutions, we provide comprehensive Linux server hardening services designed to secure, optimize, and future-proof your infrastructure. Our certified Linux experts follow industry best practices to safeguard your systems, enhance performance, and ensure compliance.
Here’s how we fortify your Linux environment:
With KV IT-Solutions, your Linux servers are not just protected—they are fortified, ensuring that your business runs smoothly, your data stays safe, and your compliance requirements are always met.
Why Linux Server Hardening is Critical
Our Approach to Linux Server Hardening
Assessment – Analyze server configurations, vulnerabilities, and risks.
Planning – Develop a customized hardening strategy tailored to your business needs.
Implementation – Secure operating systems, services, network, users, and applications.
Validation & Testing – Conduct security audits, penetration tests, and compliance checks.
Ongoing Monitoring & Updates – Continuous patching, monitoring, and optimization.
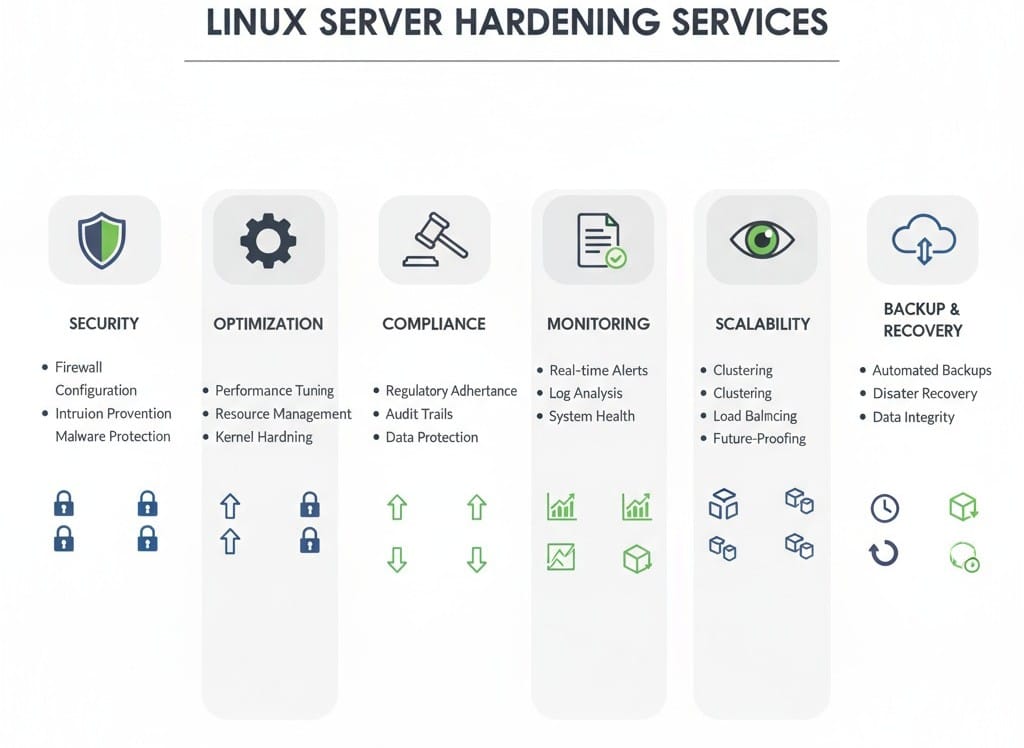
Core Linux Server Hardening Services
At KV IT-Solutions, we offer comprehensive Linux server hardening services designed to protect your systems, optimize performance, and maintain compliance. Each service focuses on securing a critical layer of your Linux environment while ensuring smooth, efficient operations.
1. User & Privilege Management
Proper user and privilege management ensures that only authorized personnel can access sensitive system resources, reducing the risk of unauthorized changes or breaches.
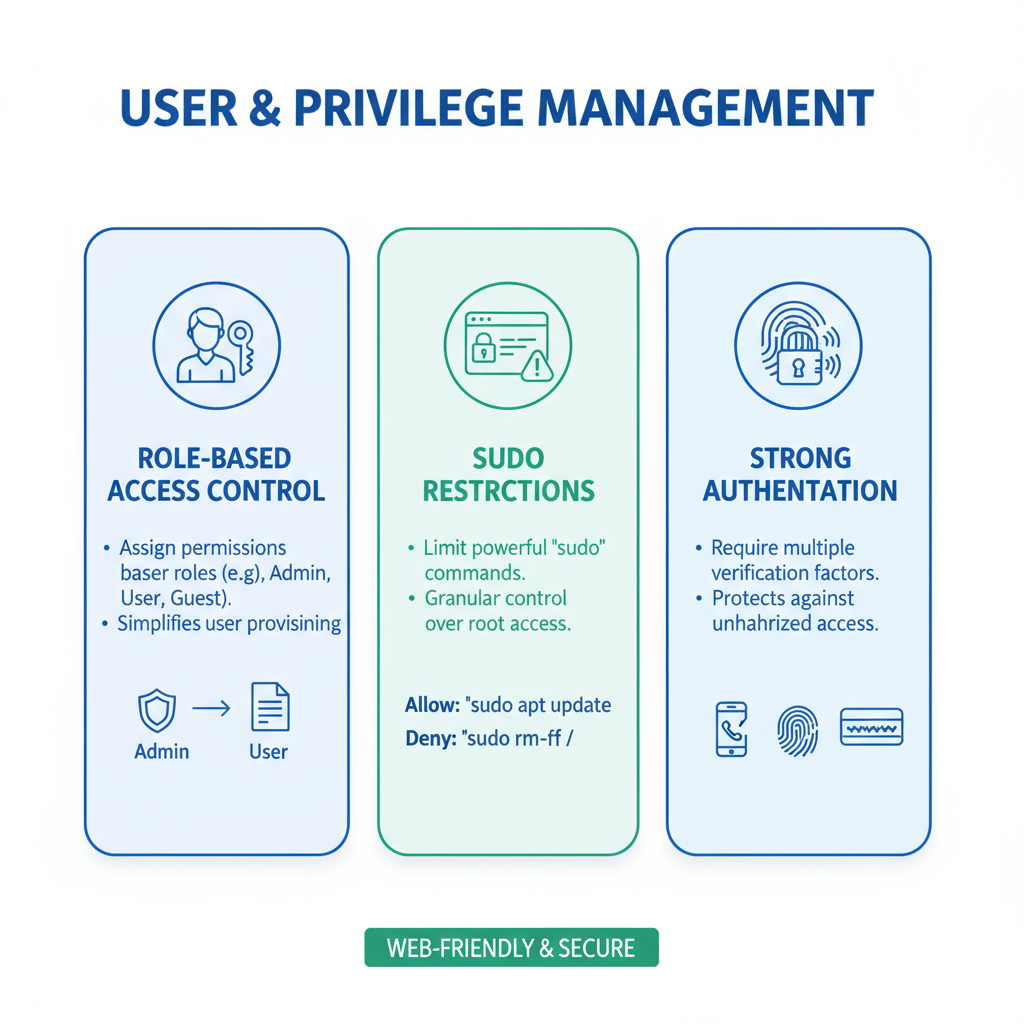
Impact: Strong user and privilege management minimizes security risks by ensuring only the right people have the right access at the right time.
2. Service & Daemon Hardening
Securing running services and daemons reduces the attack surface of your servers and protects critical processes.
.png)
Impact: Service and daemon hardening reduces the attack surface and safeguards critical system processes from exploitation.
3. Network Security & Firewall Configuration
Linux network hardening protects your servers from external and internal threats, ensuring only legitimate traffic reaches your systems.
.png)
Impact: Robust network security and firewall configuration ensure only trusted traffic enters your systems, protecting against internal and external threats.
4. Patch Management & Compliance
Keeping your systems updated and compliant ensures protection against known vulnerabilities while meeting industry regulations.
.png)
Impact: Effective patch management and compliance safeguard systems from known vulnerabilities while ensuring adherence to industry regulations.
5. Kernel & System Performance Optimization
Server hardening also involves tuning the system for maximum efficiency and reliability.
.png)
Impact: Kernel and system performance optimization boosts efficiency, reliability, and scalability to handle workloads seamlessly.
6. Advanced Security Techniques
For enhanced protection, we implement additional layers of security that defend against sophisticated threats.
.png)
Impact: Advanced security techniques add multiple protective layers, defending systems against sophisticated threats and ensuring data integrity and continuity.
Advanced Hardening Techniques
Benefits of Partnering with KV IT-Solutions
- Reduced Attack Surface – Proactive threat mitigation
- Compliance-Ready Systems – Audit-ready infrastructure for regulatory standards
- Optimized Server Performance – High uptime, low latency, efficient resource use
- 24/7 Monitoring & Support – Continuous vigilance and expert intervention
- Future-Ready Infrastructure – Scalable, secure, and resilient Linux environment
Challenges Without Proper Server Hardening
FAQs Linux Server Hardening
Core Linux Infrastructure Security Capabilities

"Secure. Optimize. Comply. — Harden Your Linux Servers with KV IT-Solutions Today!"
Protect, optimize, and future-proof your Linux servers with KV IT-Solutions. Our expert server hardening services reduce risk, ensure compliance, and enhance performance—so your IT infrastructure is secure, resilient, and ready for growth.
Testimonials
 Enquiry Now
Enquiry Now











